In this article, we will see how to Setup key-based authentication on SSH. And how to connect SSH using key based authentication.
SSH (Secure Shell) is a secure network protocol. It is used to establish a secure connection between server and client to handle the server remotely. It supports two kinds of authentication mechanisms.
Read Also: How to Install Webuzo Control Panel on CentOS 7
It supports two kinds of authentication mechanisms.
- Password based Authentication
- Public Key based Authentication
Setup Key-Based Authentication In SSH
To set up a Key-Based SSH login in Linux, you have to generate a public authentication key and add it to the file ~/.ssh/authorized_keys on a remote server.
The below steps will explain to you properly how to generate the public key. And add it to a remote server.
First check if you already have public key
Before generating a new pair of public keys we should check first if the public does not already exist. If we already have one, we can use that key as well and we should skip overwriting that existing key.
To check for the existing public keys run the below command:
ls -al ~/.ssh/id_*.pub
The above command either will give you an error something like No such file or directory or no matches found. in that case, you don’t have any existing key. but if you get a list with a key you either take a backup and generate a new key or skip this step and follow the next one directly.
As for this article, we are assuming that you do not have any existing key so let’s move forward to generate a new one.
Generate a new public key pair for SSH.
To generate the key run the following command it will generate new 4096 bits key pair and add your email id as a comment:
ssh-keygen -t rsa -b 4096 -C "[email protected]"
Press Enter Key to choose default filename and default location to save the file:
Enter file in which to save the key (/home/username/.ssh/id_rsa):
After that, you will be asked to type a passphrase. A passphrase is a kind of password to increase the security on file. If you choose to set the passphrase you have to save the passphrase for future use. Whenever you will use the key you will be asked to enter a passphrase. if you want to use this authentication to automate some processes ignore this passphrase and just press Enter.
Enter passphrase (empty for no passphrase):
You can find the image below to see how the process will look like:
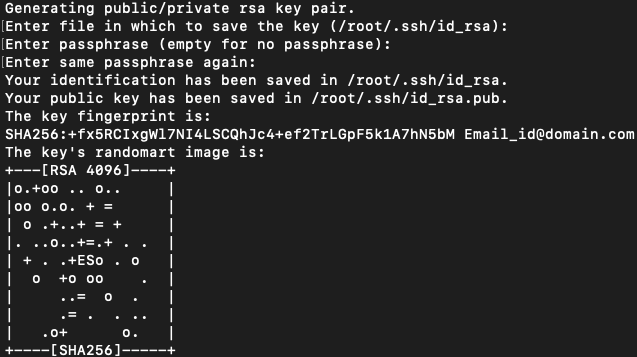
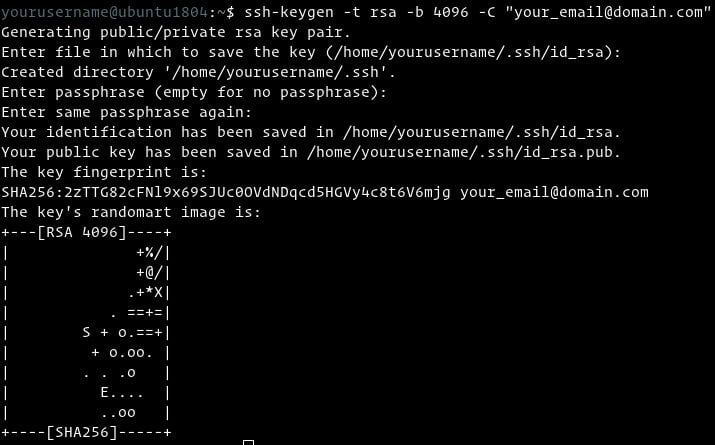
To be sure that the SSH keys are generated you can list your new private and public keys with:
ls -l ~/.ssh/id_*
-rw-------. 1 username username 3247 Aug 15 14:39 /root/.ssh/id_rsa -rw-r--r--. 1 username username 745 Aug 15 14:39 /root/.ssh/id_rsa.pub
Copy the public key
We have generated the SSH key pair, Now to access the server without a password we need to copy the public key on a remote server. The quickest method to copy our public key on a remote server is to use the command ssh-copy-id. So run the below command to do that:
ssh-copy-id server_username@server_ip_address
You will be asked to enter the server_username password:
server_username@server_ip_address's password:
When you will be authenticated our generated public key will be automatically added to ~/.ssh/authorized_keys the file and you will exist from the server.
Now if due to some reason you are not able to use ssh-copy-id if you don’t have direct access to the server and some other admin is handling the server at the moment and asking your public key to allow you server access without giving a password, then you need to follow these below steps. these are manual steps you can follow:
- Get you public key and copy it:
cat ~/.ssh/id_rsa.pub
The above command will display your public key content so copy that content, Now if you don’t have the server directly and someone asking for your public key. just give him the output of the above command that is the content of the file.
- You have server access, then login to server:
ssh server_username@server_ip_address
Login by the above command and then open the file ~/.ssh/authorized_keys with your favorite editor and add your public key at the end of the file which we copied earlier that was presented in ~/.ssh/id_rsa.pub.
vim ~/.ssh/authorized_keys
Login to your server using SSH keys
We have completed the steps that allow us to log in on the server without a password. So to test those just login on server with the below command:
ssh server_username@server_ip_address
If you have followed the steps very well you should be logged in without a password.
Disabling SSH Password Authentication
Now as can log in on the server without a password, So to increase the security we can now disable the password-based authentication for SSH.
Before starting the process to disable the SSH password-based authentication just test if you can log in on a server without a password or not also verify if the user you are logged in with has sudo privileges or not. As it should have sudo privileges to perform this password disable changes.
Now login to the server with key based authentication either with root or sudo privileged user.
ssh server_username@server_ip_address
Now open the SSH configuration file /etc/ssh/sshd_config in your favorite editor and make these below changes.
Open file by below command:
vim /etc/ssh/sshd_config
Make these below changes accordingly.
PasswordAuthentication no ChallengeResponseAuthentication no UsePAM no
To Disable the SSH Authentication and allow Password Authentication for a particular user.
Match User linuxpanda
PasswordAuthentication Yes
When done save and close the file and restart the ssh service as below according to OS.
On Ubuntu/Debian distributions, run the below command:
sudo systemctl restart ssh
On CentOS/Fedora/RHEL distribution, run the below command:
sudo systemctl restart sshd
Conclusion
We have gone through the article and have seen how to Setup Key-based authentication on SSH. It allows us to log in to the server without a password. This also helps to increase the security on the server if we disable the password authentication from SSH configuration and restart the ssh command.
If you have any queries you can ask us, just comment on your query below.

















Leave a Reply