In this tutorial, we will learn how to install and use the Maldet package to detect viruses on CentOS 8 Linux Operating System.
Malware is a type of virus that includes spyware, ransomware, etc. It is designed to damage the system, access and delete the private data, gain unauthorized access. Maldet (Linux Malware Detect) is one of the most popular packages which is used to detect malware and scan malicious files in the server.
Prerequisite for Install and run a malware scan
- CentOS 8 Server
- Root access or Other User with Sudo privileges
Let’s Install Maldet on CentOS 8
- To Install epel repository
yum install epel-release -y
- Now to Install DNF package.
yum install dnf -y
- Maldet require Perl because Maldet is written in Perl.
dnf install perl -y
- Install wget package
yum install wget -y
- Download the latest version of Maldet
wget http://www.rfxn.com/downloads/maldetect-current.tar.gz
- Extract the downloaded file
tar -xvzf maldetect-current.tar.gz
- Open the extracted directory and run install script.
cd maldetect-1.6.4 && sh install.sh
After successful installation, it will show an output screen like this.
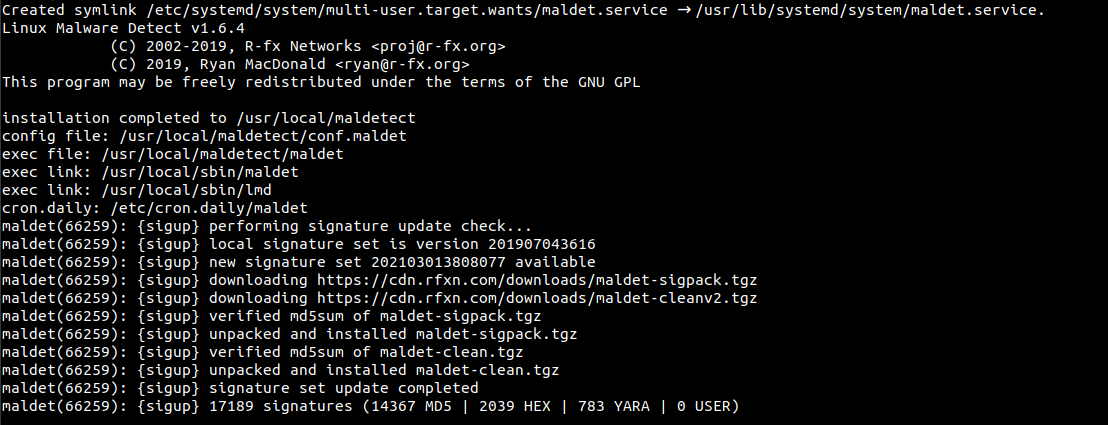
Maldet Syntax
The Syntax of Maldet is as follows:
maldet [OPTION] [Directory Path]
Explanation of Maldet options:
- -b (–background) : It is used to execute the operations in background.
- -u (–update) : It is used to update malware detection signature from rfxn.com.
- -d (–update-ver) : It is used to update the Maldet version from rfxn.com.
- -m (–monitor USERS|PATHS|FILE) : Run maldet with inotify kernel level file create/modify monitoring.
- -k (–kill) – Terminate inotify monitoring service
- -r (–scan-recent PATH DAYS) : Scan files created/modified in the last X days (default: 7d, wildcard: ?)
- -l (–log) : It is to check the Maldet log file events.
- -a (–scan-all PATH) : This option will scan all files in the path.
- -c (–checkout FILE) : Upload suspected malware to rfxn.com for review & hashing into signatures
- -e (–report SCAN ID email) : View scan report of most recent scan or of a specific SCAN ID and optionally e-mail the report to a supplied e-mail address. Example – maldet –report, maldet –report list, maldet –report 050910-1534.21135, maldet –report SCAN ID [email protected]
- -s (–restore FILE|SCAN ID) – Restore file from quarantine queue to original path or restore all items from a specific SCAN ID, maldet –restore /usr/local/maldetect/quarantine/config.php.23754, maldet –restore 050910-1534.21135
- -p (–purge) : This option will clear logs, session and temporary data.
- -U (–user USER) : Set execution under specified user, ideal for restoring from user quarantine or to view user reports. Example – maldet –user nobody –report, maldet –user nobody –restore 050910-1534.21135.
- -q (–quarantine SCAN ID) : This option will quarantine all malware from the report.
- -n (–clean SCAN ID) : This option will clean & restore malware hits from the report.
Configure Maldet on CentOS 8
Edit the Maldet configuration file “/usr/local/maldetect/conf.maldet”
vim /usr/local/maldetect/conf.maldet
Find and change the following lines as per your needs:
# To enable the email notification. email_alert="1" # Specify the email address on which you want to receive an email notification. email_addr="[email protected]" # Enable the LMD signature autoupdate. autoupdate_signatures="1" # Enable the automatic updates of the LMD installation. autoupdate_version="1" # Enable the daily automatic scanning. cron_daily_scan="1" # Allows non-root users to perform scans. scan_user_access="1" #move hits to quarantine & alert quarantine_hits="0" # Clean string based malware injections. quarantine_clean="0"
When done, Save and close the file.
Scan Directory with Maldet
- Scan any directory with -a option. For example to scan the directory /home/
maldet -a /home/
From the above screen, you will get the scan report ID.
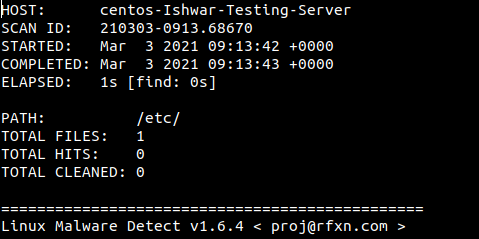
- To see the Report run the following command.
maldet --report 210303-0913.68670
You should see the scan report on the following screen:
- To quarantine the infected files, run the following command
maldet -q 210303-0913.68670
If you want to clean on all malware results from a previous scan, run the following command:
- To clean the infected files from a previous scan
maldet --clean 210303-0913.68670
Scan Directory with Maldet in Background
- If we want to run the scan process in the background the use -b option.
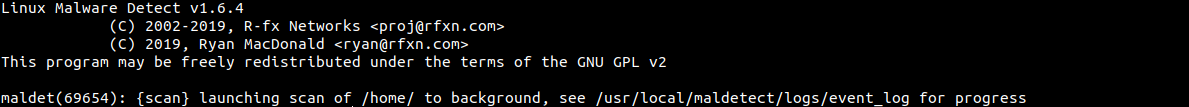
For Example, we will scan the /home/ in the background
maldet -b -a /home/
You will see the output screen like this:
- To check the status of scan you can check the event_log file
tail -f /usr/local/maldetect/logs/event_log
You should see the following output screen with the report ID.
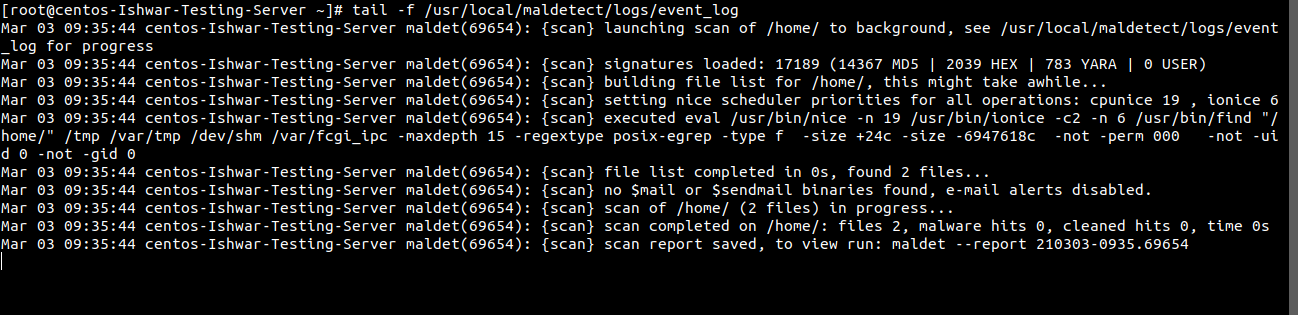
To see the Report run the following command with Report ID:
maldet --report 210303-0935.69654
Clear Logs and Temporary data
- To clear logs, quarantine queue, session and temporary data from the previous scan run the following command:
maldet -p
- You will see the following output screen:
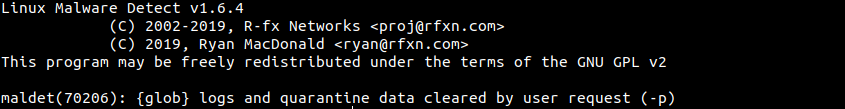
- You can verify the log data by running the following command:
maldet -l
Conclusion
In this tutorial, we have learned how to install, perform scanning on the server to detect the malware and remove the malware.
If you guys have any queries related to this Install and run a malware scan tutorial, Let me know in the comments.

















Leave a Reply